What is HSDFSDCrypt ransomware? And how does it implement its attack?
HSDFSDCrypt ransomware is a new ransomware infection which was first spotted on the 6th of November, 2017. This ransomware mainly targets German users. According to researchers, HSDFSDCrypt is installed on the computer through corrupted macro scripts which are embedded into fake messages from Amazon, PayPal, Internet and electricity suppliers. HSDFSDCrypt ransomware functions similarly to DolphinTear ransomware and Versiegelt ransomware – the only difference between HSDFSDCrypt and the aforementioned file-encrypting threats is that HSDFSDCrypt ransomware does not add any file marker to the encrypted files as it removes all indications of the files to a nonsensical string of characters which is why this ransomware’s name is kind of odd.
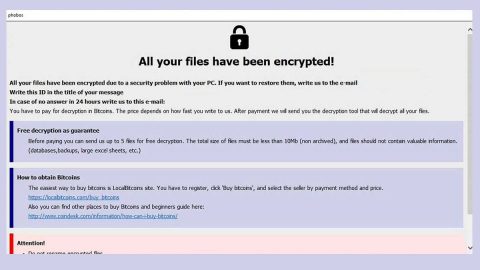
After infecting the targeted system, the ransowmare encodes all the files it can find in the computer using both modified AES and RSA ciphers at the same time renaming the original file names of the files with some set of random characters. As you know, ransomware threats like HSDFSDCrypt changes the structure of data containers. As a result, you won’t be able to access data such as photos, databases, multimedia content, documents, eBooks and a whole bunch of other file formats. Once it finishes encrypting all the targeted files, HSDFSDCrypt ransomware drops a file named Wo_sind_meine_Dateien.html – the file named means, “Where_is_my_data.html” which contains the ransom note written in German. Its ransom note appears right after it makes sure that all the shadow volume copies of the encrypted files are deleted so as to prevent users from restoring them using the Windows Previous version feature.
Here’s the ransom note created by HSDFSDCrypt ransomware as translated on English:
“Your files have been encrypted!
Dear Sir or Madam,
As you’ve already noticed, all your files have been encrypted.
How do I get access to my files?
To successfully decrypt your files, you need our special software and its decrypt key.
Where can I get the software?
The decryption software can be purchased from us.
The price for the decryption software is 0.12 Bitcoin.
Please note that we only accept Bitcoin for the purchase of the software.
[edit: instructions on how to purchase Bitcoin from respected markets]
ATTENTION!
If we do not notice any payment within 7 days, we assume that you are not interested in decrypting your files. In that case, we will irrevocably delete the decrypt key and your files will be lost forever.
Your files were encrypted with military quality using a 256-bit AES algorithm. We do not recommend wasting time decrypting yourself, it would only cost you extra time and money, but your files would still be encrypted.
bonus
In addition to the decryption software, after successful payment, you will receive instructions on how the malware could reach your system and how you can protect yourself from further attacks in the future!”
Even though there’s no way for you to recover your files easily, that does not mean you have to pay the demanded as it is not the best solution – in fact it’s probably the worst solution to recover your files. Your best choice would be is to use whatever backup copies you have of the affected files and wait until a free decryption tool is available.
How is HSDFSDCrypt’s malicious payload distributed online?
You can stumble upon HSDFSDCrypt’s malicious payload when you open an email which is supposedly sent by Amazon, PayPal and other well-known companies or groups. Cyber crooks often disguise their malicious payload as something that is sent from Amazon or PayPal to trick users into downloading and opening the macro-enabled document which contains malicious script that opens and installs HSDFSDCrypt ransomware into the targeted computer.
Delete HSDFSDCrypt ransomware right away using the removal instructions below.
Step 1: Tap Ctrl + Shift + Esc keys to open the Task Manager.

Step 2: After opening the Task Manager, look for Windows Desktop.exe which is HSDFSDCrypt ransomware’s malicious process, right click on it and select End Process or End Task.

Step 3: Close the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.
Step 4: Look for HSDFSDCrypt ransomware or any suspicious program and then Uninstall it/them.

Step 5: Tap Win + E to launch File Explorer.
Step 6: After opening File Explorer, navigate to the following locations below and look for HSDFSDCrypt ransomware’s malicious components such as the ransom note Wo_sind_meine_Dateien.html as well as the macro-enabled document file responsible for installing the crypto-malware in your computer.
- %AppData%
- %Local%
- %Temp%
- %Roaming%
- %LocalLow%
Step 7: Close the File Explorer. Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step 8: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 9: Navigate to the listed paths below and look for the registry keys and sub-keys created by HSDFSDCrypt ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step 10: Delete the registry keys and sub-keys created by HSDFSDCrypt ransomware.
Step 11: Close the Registry Editor.
Step 12: Empty your Recycle Bin.
To make sure that HSDFSDCrypt is completely removed and that nothing is left behind, use the following antivirus program. To use it, refer to the instructions below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOSscreen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Optionuse the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Boxwill show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. Installation will start automatically once download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.