What is Mcold ransomware? And how does it implement its attack?
Mcold ransomware, also known as [email protected] ransomware, is a file-encrypting threat that could leave files inaccessible to users. At first, security experts thought that it’s another one of the new variants of GlobeImposter ransomware but it turns out that it is actually the latest variant of Maoloa ransomware as it contains similar code snippets. In fact, it implements its attack the same way as the Maoloa ransomware does.
The instant it invades a targeted machine, Mcold ransomware will drop its malicious payload which initiates the attack by connecting the computer to a remote server. After that, it downloads its malicious components and drops them on several system folders which are used to manipulate system processes, and employs several modules like the information gathering module and stealth protection module.
It first employs the information gathering module which gathers information from the computer. The information gathered may consist of machine identification data and the personal information of the user. The collected information is then used to bypass any security software in the system by looking for engines of applications that can block the attack of Mcold ransomware.
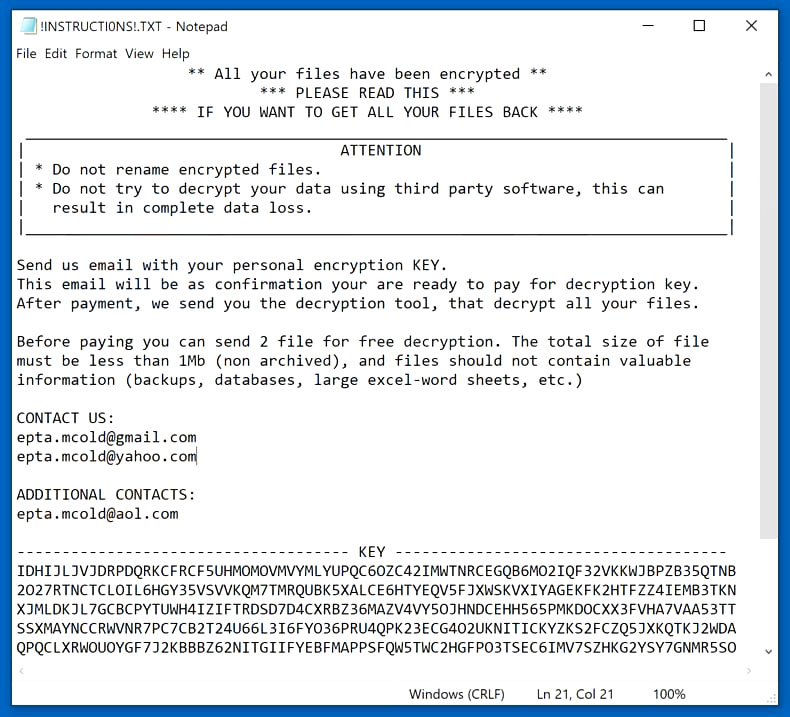
Additionally, it also modifies the Windows Registry by modifying existing entries and creating new ones to allow it to run automatically each time the infected computer is turned on. After these system changes, it starts the encryption using a sophisticated encryption algorithm and once the encryption is finished, it appends the “.[[email protected]]” suffix to each one of the encrypted files. It then drops a text file named “!INSTRUCTIONS!.txt” which contains the following content:
“** All your files have been encrypted **
*** PLEASE READ THIS ***
**** IF YOU WANT TO GET ALL YOUR FILES BACK ****
___________________________________________________________________________________________
| ATTENTION |
| * Do not rename encrypted files. |
| * Do not try to decrypt your data using third party software, this can |
| result in complete data loss. |
|___________________________________________________________________________________________ |
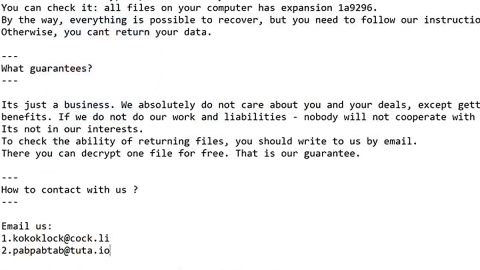
Send us an email with your personal encryption KEY.
This email will be as confirmation you are ready to pay for the decryption key.
After payment, we send you the decryption tool, that decrypts all your files.
Before paying you can send 2 files for free decryption. The total size of the file
must be less than 1Mb (non-archived), and files should not contain valuable
information (backups, databases, large excel-word sheets, etc.)
CONTACT US:
[email protected]
[email protected]
ADDITIONAL CONTACTS:
[email protected]
————————————- KEY ————————————-
EFLNUW6RCNGXJOBXRNJ4JETCGDCJ6ZN76WWLKAG5YHLT27AUNXU7B3GH6HRQCQETOZIVIXSOOBCHUMPA
DAEOQIZAV65ADDWVEPZOCCWH43TKS7PL7LLZCCUYR6GWHTYSGO4RPF5HJLSVMMGUWUH5Y52SKH4MFAP6
MQ5BDWXAGZMEHDCMXUSLAZADOZYPEAIIZC7YU3XIUJQQPOSPPMYGNP4FB7KLAI4T4WXO4ZBD4LBBN7HQ
GFBPPLZ3PV2FXM3FTNCOUAVDFYYWCRIRRO4FBDB3XM3SOGL3MV6D2PZQLXQD2BN3FBXK2XBAIV2AA6WP
GWWHAIN3BBNNEHT4RTGVP6MENW7BFGQTGN3ZEAAL7KDUU6IIEVA6WNFBWXJWGY6XNKXB2745AGNJENWT
KVUBT5XBIV54OJ6FR5JLKIQ5ZDM6WKYYFLU2Z3PQLSLGXSEHWPPWH732HQFNPYP2HKMERQCBZ4FGYM7K
GRWA2QH4BYPOCYM4OEF2QCTKNPWAMXYQKZ2RAV2NVS5UBZ6HDKYRBJQTOY2QHPDU34G2F7I6YG7PARTZ
TJOZMOOZKDW6UBUY726ALVPXN4C3PQTFOSZENXV2IXT323KFI43NPD6GQX4JKTDAZLCD65FK7PZWXICQ
EEVGHZML4YIBSZLLCDXYKBIQ6SVQCDNWOL5WBN36KHR3JTWM3UTXIOPNHMNNWMCRJI26I4IXIENDUE73
247K7PUVS5OOVMBSWAHZKHRI2OBOCZFNXR56QX3ZHLRNXBFFGFRKXOJPEAU7II5XT24AY3LSUCACNJVV
DNRPQIMCGWOLPZECZO5A=
——————————————————————————-”
How does Mcold ransomware spread online?
At the time of writing, it isn’t clear yet how Mcold ransomware spread online. However, its creators may be using several techniques. For one, it could spread via malicious spam email campaigns where crooks attach an infected link or file. Usually, the email is disguised as something urgent to trick users into opening them and clicking the link or downloading the infected file attached to it. This is why you need to be more cautious in opening emails no matter who the sender is.
Terminate Mcold ransomware from your infected computer with the help of the following removal guide.
Step_1: First, tap the Ctrl + Shift + Esc keys on your keyboard to open the Task Manager.
Step_2: After opening the Task Manager, go to the Processes tab and look for any suspicious-looking process that takes up most of your CPU’s resources and is most likely related to Mcold ransomware.
Step_3: After that, close the Task Manager.
Step_4: Tap Win + R, type in appwiz.cpl and click OK or tap Enter to open Programs and Features under Control Panel.
Step_5: Under the list of installed programs, look for Mcold ransomware or anything similar and then uninstall it.
Step_6: Next, close the Control Panel and tap Win + E keys to launch File Explorer.
Step_7: Navigate to the following locations below and look for Mcold ransomware’s malicious components such as “!INSTRUCTIONS!.txt” and “[random].exe” and other suspicious files, then delete all of them.
- %TEMP%
- %WINDIR%\System32\Tasks
- %APPDATA%\Microsoft\Windows\Templates\
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step_8: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech-savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you trouble and time, you can just use Restoro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step_9: Tap Win + R to open Run and then type in Regedit in the field and tap enter to pull up Windows Registry.
Step_10: Navigate to the following path:
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step_11: Delete the registry keys and sub-keys created by Mcold ransomware.
Step_12: Close the Registry Editor and empty the Recycle Bin.
Try to recover your encrypted files using the Shadow Volume copies
Restoring your encrypted files using Windows Previous Versions feature will only be effective if Mcold ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.
Congratulations, you have just removed Mcold Ransomware in Windows 10 all by yourself. If you would like to read more helpful articles and tips about various software and hardware visit fixmypcfree.com daily.
Now that’s how you remove Mcold Ransomware in Windows 10 on a computer. On the other hand, if your computer is going through some system-related issues that have to get fixed, there is a one-click solution known as Restoro you could check out to resolve them.
This program is a useful tool that could repair corrupted registries and optimize your PC’s overall performance. Aside from that, it also cleans out your computer for any junk or corrupted files that help you eliminate any unwanted files from your system. This is basically a solution that’s within your grasp with just a click. It’s easy to use as it is user-friendly. For a complete set of instructions in downloading and using it, refer to the steps below
Perform a full system scan using Restoro. To do so, follow the instructions below.