What is Spiteful Doubletake ransomware? And how does it implement its attack?
Spiteful Doubletake ransomware is a data-encrypting virus discovered recently. It is created based on the Perl programming language and is believed to be in its early development phase. It supports both the Blowfish cipher and the Cipher Block Chaining or CBC mode of operation.
Once Spiteful Doubletake ransomware infects your computer, it will implement a series of modifications starting by connecting the computer to a Command and Control server. This server is managed by the attackers and is where the other components will be downloaded. Once these malicious components are downloaded, they will be placed into system folders. They are then used to execute the data harvesting module which collects information from the system. The information obtained will be used in the second module called stealth protection. This second module is used to scan the system for strings of antivirus programs, a sandbox environment, and security programs.
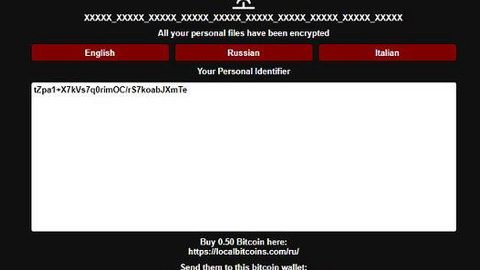
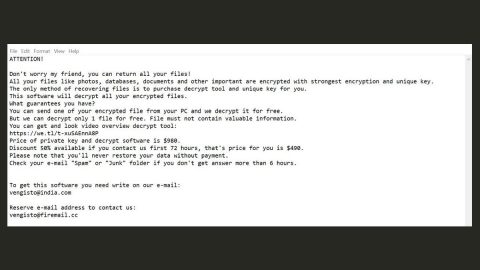
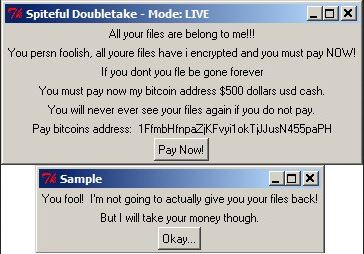
Moreover, Spiteful Doubletake ransomware also alters the Windows Registry, allowing it to execute its attack automatically every time you turn on your computer. After it achieves persistence, Spiteful Doubeltake ransomware will start the encryption with the targeted files. It mostly targets user-generated files like videos, images, documents, databases, audio files, and many more. After the encryption, it adds the .enc extension to all encrypted files. It then changes the desktop background with a flashing message in red on a black background saying, “DO NOT HALT OPERATION – FILE CORRUPTION WILL OCCUR”. Aside from that, it also opens a dialog box labeled “Spiteful Doubletake – Mode: LIVE” that reads:
“All your files are belonging to me!!!
You person foolish, all your files have I encrypted and you must pay NOW!
If you don’t your file be gone forever
You must pay now my bitcoin address $500 dollars USD cash.
You will never ever see your files again if you do not pay.
Pay bitcoin address [random characters]
[Pay Now!?BUTTON]’
Clicking the ‘Pay Now’ button triggers a new dialog box titled ‘Sample’ to appear, which says:
‘You fool! I’m not going to actually give you your files back!
But I will take your money though.
[Okay…|BUTTON]”
And if you click on the “Pay Now” button, it will trigger a new dialog box labeled “Sample” containing a message that says:
“You fool! I’m not going to actually give you your files back!
But I will take your money though.
[Okay…|BUTTON]”
You must not give in to the ransomware’s demands. There is no point in paying the ransom if you can’t recover your files. The best thing you can do is to wipe out this pesky crypto-virus from your computer the soonest way you can.
How is the malicious payload of Spiteful Doubletake ransomware disseminated?
The malicious payload of Spiteful Doubletake ransomware is disseminated using various techniques. One of the commonly used techniques is via spam emails. The payload file of this crypto-virus is attached to emails and sent to potential victims via spambots. This file may be a PDF file, ZIP file, or a document containing malicious scripts that installs Spiteful Doubletake ransomware in the system.
You need to wipe out Spiteful Doubletake ransomware from your computer using the removal instructions provided below.
Step_1: Close the program window of Spiteful Doubletake ransomware. If you find it hard to do so, you can close it via Task Manager. Just tap Ctrl + Shift + Esc keys to launch the Task Manager.
Step_2: Next, go to the Processes tab and look for the malicious process of Spiteful Doubletake ransomware. Such processes typically consume a high amount of system resources and are named randomly so you need to beware of them. Once you found these processes, right-click on each one of them and select End Process or End Task.
Step_3: Close the Task Manager and open Control Panel by pressing the Windows key + R, then type in “appwiz.cpl” and then click OK or press Enter.
Step_4: Look for dubious programs that might be related to Spiteful Doubletake ransomware and then Uninstall it/them.
Step_5: Close Control Panel and then tap Win + E to launch File Explorer.
Step_6: After opening File Explorer, navigate to the following directories below and look for Spiteful Doubletake ransomware’s malicious components such as Spiteful DoubletakeRansomware.exe, [random].exe, and other suspicious-looking files and then erase them all.
- %TEMP%
- %APPDATA%
- %DESKTOP%
- %USERPROFILE%\Downloads
- C:\ProgramData\local\
Step_7: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech-savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you trouble and time, you can just use Restoro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step_8: Tap Win + R to open Run and then type in Regedit in the field and tap enter to pull up Windows Registry.
Step_9: Navigate to the listed paths below and look for the registry keys and sub-keys created by Spiteful Doubletake ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step_10: Delete the registry keys and sub-keys created by Spiteful Doubletake ransomware.
Step_11: Close the Registry Editor.
Step_12: Empty your Recycle Bin.
Try to recover your encrypted files using their Shadow Volume copies
Restoring your encrypted files using Windows Previous Versions feature will only be effective if Spiteful Doubletake ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.
Congratulations, you have just removed Spiteful Doubletake Ransomware in Windows 10 all by yourself. If you would like to read more helpful articles and tips about various software and hardware visit fixmypcfree.com daily.
Now that’s how you remove Spiteful Doubletake Ransomware in Windows 10 on a computer. On the other hand, if your computer is going through some system-related issues that have to get fixed, there is a one-click solution known as Restoro you could check out to resolve them.
This program is a useful tool that could repair corrupted registries and optimize your PC’s overall performance. Aside from that, it also cleans out your computer for any junk or corrupted files that help you eliminate any unwanted files from your system. This is basically a solution that’s within your grasp with just a click. It’s easy to use as it is user-friendly. For a complete set of instructions in downloading and using it, refer to the steps below
Perform a full system scan using Restoro. To do so, follow the instructions below.