What is Zuahahhah Ransomware?
The Zuahahhah Ransomware is one of the cyber threats that uses cryptographic algorithms to alter focused data and make a requirement for a decoding software, which is mainly offered by its developers. The Zuahahhah Ransomware is named a record encoder Trojan that is designed to encrypt documents on your system and then later offer you access to a decryption service and the code once you pay the fee to a specific Bitcoin wallet address. Beginning threat examination revealed that the Zuahahhah Ransomware is the later version of the Aviso Ransomware or otherwise called the Crypt888 Ransomware.
How does the Zuahahhah Ransomware infect a computer?
When the Zuahahhah Ransomware infects a computer, the Zuahahhah Ransomware will communicate with its Command and Control server to send information about the infected computer to the people operating the Zuahahhah Ransomware. The Zuahahhah Ransomware will run the executable file with appended name ‘server.exe’ on the infected file on your computer. During its attack, the Zuahahhah Ransomware will simply modify the infected computer’s Desktop image so it can deliver its ransom note. Using a mixture of the AES and RSA encryptions, the Zuahahhah Ransomware will encrypt the victim’s files and then encrypt the encryption key itself, which means that the victim will not be able to recover the decryption key necessary to restore the affected files if the said amount is not paid. This is a the usual encryption method used by these threat creators.
How does this Zuahahhah Ransomware spread?
Developers of the crypto-malware rarely rely on only one distribution method, but they normally take advantage of several strategies in order to attack as many computeras possible. Not only the majority of file-encrypting viruses share similar features, but also they spread similarly. These are the most common ransomware distribution ways:
- malicious spam emails and their attachments,
- malvertising,
- fake/illegal downloads,
- fake updates,
- exploit kits.
The biggest chances to get infected with ransomware is by clicking on a malicious email attachment or any other interactive content included in the letter from an unknown and questionable sources, for instance, a link or button. These crooks use social engineering tactics at any cost and convince people that the letter is sent from the reliable institution that encourages to open the document and check the information provided in particular website.
Thus, you should always be careful opening emails from unknown sources and do not forget other security tips, such as download only legal software, install updates directly from the publisher’s site, avoid visiting high-risk websites and keep programs and OS updated.
How does Zuahahhah Ransomware works?
When a client is infected by the Zuahahhah Ransomware Trojan, a report including the dynamic username, IP address and OS version is sent to the threat’s ‘Command and Control’ servers. The Zuahahhah Ransomware is accounted for to keep running as “server.exe” on tainted computers and alters the desktop background image as an approach to deliver the ransom warning to the user. The Trojan primarily creates a couple of encryption and decryption keys, which are likely just basic for its operations. The threat is accounted for to apply an AES-256 cipher to the target data directly, and the decryption key is subjected to an encryption procedure with the RSA-2048 cipher to ruin or stop the attempts of data recovery. The double encryption method permits threats like Zuahahhah Ransomware and the RanDsomeWare Ransomware keep computer system security specialists from building a decryptor for the traded off clients. The Zuahahhah Ransomware is probably going to encipher information containers utilized by clients to store important files such as the family photographs, recordings, music, databases, presentations, eBooks, spreadsheets and text.
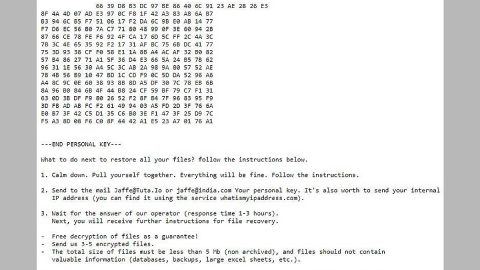
Ransom note of the Zuahahhah Ransomware :
Shown below is the payoff notice exhibited as a desktop background image and offers the following text:
‘YOUR FILES HAS BEEN LOCKED
ZUAHAHHAH
Your Computer has been Get:
– password your account
– email account
– files your computer
– delete your files’
How to manually delete Zuahahhah Ransomware?
- Find the {unknown name}.exe file that represents the launcher.
- Right-click the file and choose Delete.
- Simultaneously tap Win+E to launch Windows Explorer.
- Type %TEMP% into the bar at the top and tap Enter to access the directory.
- Right-click and Delete the copy (could be named x.exe) of the launcher.
- Type %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup into the bar at the top and tap Enter.
- Right-click and Delete the shortcut file named Microsoft Update.lnk.
- Empty Recycle Bin and then initiate the decryption of your personal file.
How to automatically remove Zuahahhah Ransomware?
These instructions indicate how to get rid of Zuahahhah Ransomware automatically. The instructions need to be applied on the infected computer.
- Turn the infected computer on. If it is turned on, restart it.
- When BIOS screen disappears after the reboot, tap F8 key repeatedly. Advanced Options menu will show up. If Windows logo appears, reboot the PC and try pressing F8 again.
- When you access Advanced Options menu, use arrow keys to navigate and choose Safe Mode with Networking. Press Enter to access the mode.

4. Wait for Windows to load Safe Mode with Networking.
5. Press and hold the Windows key and then press R key.


6. If you have pressed both keys correctly, Windows Run Box will pop up.
7. Type the following into the Open box:
explorer https://www.fixmypcfree.com/removal
- Note, that there has to be a single space gap in between iexplore and http. Click OK.
8. Internet Explorer will open and a download dialog bar will appear at the bottom of your screen. Click Run to begin the installation automatically once SpyRemover Pro is downloaded.

9. Click OK if your system asks whether you want to run SpyRemover Pro software.
10. Run SpyRemover Pro and perform a full system scan.
11. Once all the malicious infections are detected, click Fix Threats. SpyRemover Pro will ask you to register the software.
12. By registering SpyRemover Pro you will also be able to protect your computer from other potential threats. Once you have registered the program, the malware will be removed. Reboot your PC to fully implement the malware removal procedure.
“use a one click solution like SpyRemover Pro”