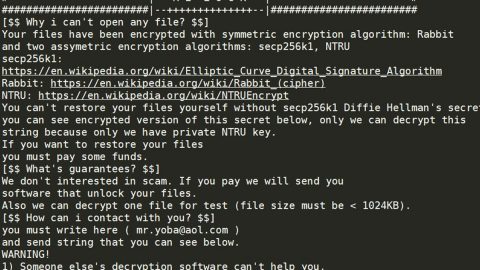
What is [email protected] ransomware? And how does it carry out its attack?
[email protected] ransomware is a new file-encrypting Trojan infection that corrupts important data stored on the infected computer and then demands a ransom from its victims. [email protected] ransomware’s first attack was observed on October 25, 2017. It behaves just like a typical ransomware infection – once this ransomware’s malicious payload is running in the computer, it initiates a sequence of malicious tasks to start its attack. One of the first things it does is to connect to its Command and Control server to send information about the infected system and download additional malicious components. Aside from that, [email protected] ransomware also creates new files in some of the important Windows system folders and proceeds to activate its malicious processes. It then starts to look for files to target, especially the ones who are generated by the user. According to researchers, it encrypts the files with the following formats:
.aif, .apk, .arj, .asp, .bat, .bin, .cab, .cda, .cer, .cfg, .cfm, .cpl, .css, .csv, .cur, .dat, .deb, .dmg, .dmp, .doc, .docx, .drv, .gif, .htm, .html, .icns, .iso, .jar, .jpeg, .jpg, .jsp, .log, .mid, .mp3, .mp4, .mpa, .odp, .ods, .odt, .ogg,.part, .pdf, .php, .kg, .png, .ppt, .pptx, .psd, .rar, .rpm, .rss, .rtf, .sql, .svg, .tar.gz, .tex, .tif, .tiff, .toast, .txt, .vcd, .wav, .wks, .wma, .wpd, .wpl, .wps, .wsf, .xlr, .xls, .xlsx, .zip.
On the encryption process, [email protected] ransomware utilizes the AES 256 cipher to leave the files unreadable along with adding the extension [email protected] on the each one of them. The ransomware delivers the decryption key to its Command and Control server and creates a text file named Readme.txt in the desktop which reads as follows:
“Access to your files was limited.
To return your files, you have 72 hours. Write to us.
Our contacts.
Our email: [email protected]
ATTENTION. To email ([email protected]) write messages only from these e-mail services. From other email services, messages may not be received by us.
Yahoo. https://mail.yahoo.com
Gmail. https://www.google.com
Mail. https://www.mail.com
ATTENTION. We will reply you within 24 hours. If there is no response from us, please send your message again.
Tor email: [email protected]
To register tor e-mail, use the service http://torbox3uiot6wchz.onion
This link opens in tor browser. Link to tor browser https://www.torproject.org/
Send us 3 encrypted files, each no more than 2 MB (only pictures, text documents or shortcuts).
We will decrypt them to you for free, to confirm that we can help you.
Together with the decrypted files you will receive further instructions.
YOUR KEY.
[260 RANDOM CHARCTERS]”
According to security experts, [email protected] ransomware may even access the Windows Registry to create new registry values which will enable its malicious processes to start whenever you start your computer. in relation to that, the same keys – “Run” and “RunOnce” will most likely be modified after the ransomware drops its ransom note. All the registry keys created by [email protected] ransomware controls all the processes that has to start when Windows is launched. It also uses them to display the ransom note after its encryption.
The time frame given by the ransomware aims to make you anxious and urge you to pay the demanded ransom as soon as you can. But you shouldn’t let these crooks get their way and for the sake of your security, it is better to stir clear in making any kind of negotiations with them.
How does [email protected] ransomware distribute its malicious payload?
As mentioned earlier, [email protected] ransomware behaves like a typical ransomware – including the way it distributes its malicious file which is through spam emails. These kinds of emails are usually disguised as legitimate messages from Amazon, PayPal, and other well-known senders. The email may contain a corrupted link or a file such as a macro-enabled document which uses malicious macro scripts to download and install [email protected] ransomware on the targeted computer.
Refer to the steps given below to eliminate [email protected] ransomware.
Step 1: Tap Ctrl + Shift + Esc to open the Task Manger.

Step 2: Once you’ve opened the Task Manager, go to the Processes tab and look for main.exe and end its process by clicking on End Task or End Process.

Step 3: Open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.
Step 4: Look for [email protected] Ransomware or any suspicious program and then Uninstall it/them.

Step 5: Tap Win + E keys to launch File Explorer.
Step 6: Navigate to the following locations below and look for [email protected] ransomware’s malicious components such as Readme.txt and the macro-enabled document it came with as well as other suspicious files and then delete all of them.
- %TEMP%
- %APPDATA%
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 7: Close the File Explorer. Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step 8: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 9: Navigate to the following path:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Step 10: Delete the registry keys and sub-keys created by [email protected] ransomware.
Step 11: Close the Registry Editor and empty your Recycle Bin.
Try to recover your encrypted files using the Shadow Volume copies
Restoring your encrypted files using Windows’ Previous Versions feature will only be effective if [email protected] ransomware hasn’t deleted the shadow copies of your files. But still, this is one of the best and free methods there is, so it’s definitely worth a shot.
To restore the encrypted file, right-click on it and select Properties, a new window will pop-up, then proceed to Previous Versions. It will load the file’s previous version before it was modified. After it loads, select any of the previous versions displayed on the list like the one in the illustration below. And then click the Restore button.

To make sure that nothing is left behind and that the [email protected] is completely removed, use the following antivirus program. To use it, refer to the instructions below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOSscreen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Optionuse the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Boxwill show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. Installation will start automatically once download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.