What is Scarab-Recme ransomware? And how does it implement its attack?
Scarab-Recme ransomware is once again another one of the new variants released by the infamous Scarab ransomware group. This new strain was recently detected and was involved in some ongoing attack that carries new versions. Just like its predecessors, it is capable of inflicting much damage to an infected computer.
Based on the analysis conducted by security experts, there is not much improvement in this new variant as it shares the same code with other new versions of Scarab. The only notable changes are the extension used which is .recme and its ransom note. Security experts have mulled over the recent happenings where Scarab has continuously released variants and came up with two possible explanations why the creators of this dangerous ransomware group keep doing so. First, it could be that these crooks are incrementally creating several versions in order to track different campaigns. Second, it could be that they are also offering customization services or have provided the source code on underground markets such as the dark web – this allows other threat actors to create their very own ransomware infection.
Once it implements its attack, it will employ a data gathering module used to collect information about the infected computer. After that, it facilitates a malicious network connection to a remote server controlled by its developers. It then starts to encrypt user-generated files. After the encryption is accomplished, it releases a ransom note that reads:
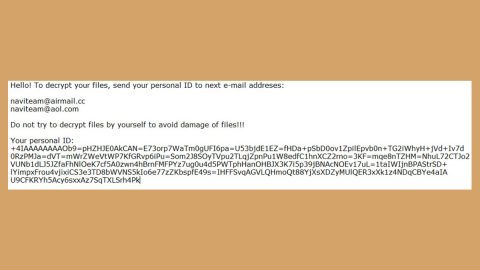
“HOW TO DECRYPT YOUR FILES
Your personal ID
6A0200000000000035858AE72592C99505310803530284C0E49FD8AF9EB9F87901A1C531B6377AD42FB576566748A91B2956
[redacted] ABA2DC929E4A511A47752FD5556FB9DC98A7E8ACAD8F4B44CE011F4967F672C8F5A5F3A6558DAE503006A47EE04130EA0E92
[redacted] DBAF8382C3D457F1924D6103A45FE06D831C30369AA60F31D89C00E26024ADFB05106FAEEA3F9A3F7DCE693213DEF3BA3AF6
[redacted] E148C8352FC89C70A1893E8ACD7D79B278D8FE544FE03C8DEF07
Your files, documents, photo, databases and all the rest aren’t
are ciphered by the most reliable enciphering.
All information about clients and their personal data was uploaded.
You must have no illusion that you can get out of this situation without our help.
You have two choices:
- Unsuccessful try to decrypt files and lose them along with the business.
- Or write to us and pay for the decryption keys and back clients files and.
We are not going to destroy your business. We show the problem on the real example.
ATTENTION! If you do not contact us within two days, the decryption keys will be destroyed and
we will send some of the files to your clients with information about your disability. They will pay
instead of you or we will put all data on the network.
Don’t waste time, the cost directly depends on the time of contact with us.
———————————————————-
You will be able to restore files so:
contact us by e-mail:
[email protected]
* report your ID and we will switch off any removal of files
(if you don’t report your ID identifier within 48 hours, decrypt key will be lost)
* you send your ID identifier and 2 files, up to 1 MB in size everyone.
We decipher them, as proof of a possibility of interpretation.
also, you receive the instruction where and how many it is necessary to pay.
you pay and confirm payment.
after payment, you receive the DECODER program. which you restore ALL YOUR FILES.”
How does Scarab-Recme ransomware proliferate?
If the theories about Scarab ransomware’s sudden increase in numbers are true then it proliferates using underground markets or the dark web where crooks are selling its source code. On the other hand, it could also spread via spam emails so you need to be careful in opening suspicious-looking emails and avoid downloading suspicious attachments.
Wipeout this new pesky Scarab strain with the help of the following removal instructions and make sure to carefully follow each one of them to successfully remove this crypto-malware from your computer.
Step 1: Tap the Ctrl + Alt + Delete keys to open a menu and then expand the Shutdown options which is right next to the power button.
Step 2: After that, tap and hold the Shift key and then click on Restart.
Step 3: And in the Troubleshoot menu that opens, click on the Advanced options and then go to the Startup settings.
Step 4: Click on Restart and tap F4 to select Safe Mode or tap F5 to select Safe Mode with Networking.
Step 5: After your PC has successfully rebooted, tap Ctrl + Shift + Esc to open the Task Manager.

Step 6: Go to the Processes tab and look for any suspicious-looking processes that could be related to Scarab-Recme ransomware and then end their processes.

Step 7: Exit the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.

Step 8: Look for Scarab-Recme Ransomware and other dubious program and then uninstall them.

Step 9: Close Control Panel and tap Win + E keys to open File Explorer.
Step 10: Navigate to the following locations and look for the malicious components created by Scarab-Recme ransomware like “HOW_TO_RECOVER_ENCRYPTED FILES.txt” and make sure to delete them all.
- %APPDATA%
- %TEMP%
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 11: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use [product-name] this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then, by all means, go on to the next steps.
Step 12: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 13: Navigate to the listed paths below and look for the registry keys and sub-keys created by Scarab-Recme ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step 14: Delete the registry keys and sub-keys created by Scarab-Recme ransomware.
Step 15: Close the Registry Editor and empty the contents of the Recycle Bin.
To ensure the removal of Scarab-Recme ransomware from your system including the malicious components it has created on your system, follow the advanced steps below.
Perform a full system scan using [product-code]. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in the URL address, [product-url] in the Run dialog box and then tap Enter or click OK.
- After that, it will download the program. Wait for the download to finish and then open the launcher to install the program.
- Once the installation process is completed, run [product-code] to perform a full system scan.