What is XIAOBA 2.0 ransomware? And how does it implement its attack?
XIAOBA 2.0 ransomware is the latest addition to the XIAOBA ransomware group. This latest variant was discovered by a researcher named Rony. Its main goal is to lock important files in an infected computer and demand ransom from its victims.
The instant it infiltrates a computer, it will drop its malicious payload which is used to connect the computer to a remote server managed by the hackers. The payload dropper of this crypto-malware has the following attributes:
SHA-256”b9f76d3201fea0b0df3e10782deb9b8d377f50a46eb7e01e17372acb5b54ed5e
Name:Uninstaller 30.0
Size:418.5 KB
After dropping its malicious payload in the system, it downloads other malicious files and place them on system folders. It then uses an information gathering module used to obtain data about the infected PC as well as its user. After obtaining data, the malicious files it downloaded early on are then used for the stealth protection module to make sure that XIAOBA 2.0 ransomware stays undetected. After these changes, it begins to scan the system for files with specific extensions such as:
.3gp, .7z, .apk, .avi, .bmp, .cdr, .cer, .chm, .conf, .css, .csv, .dat, .db, .dbf, .djvu, .dbx, .docm, ,doc, .epub, .docx .fb2, .flv, .gif, .gz, .iso .ibooks,.jpeg, .jpg, .key, .mdb .md2, .mdf, .mht, .mobi .mhtm, .mkv, .mov, .mp3, .mp4, .mpg .mpeg, .pict, .pdf, .pps, .pkg, .png, .ppt .pptx, .ppsx, .psd, .rar, .rtf, .scr, .swf, .sav, .tiff, .tif, .tbl, .torrent, .txt, .vsd, .wmv, .xls, .xlsx, .xps, .xml, .ckp, .zip, .java, .py, .asm, .c, .cpp, .cs, .js, .php, .dacpac, .rbw, .rb, .mrg, .dcx, .db3, .sql, .sqlite3, .sqlite, .sqlitedb, .psd, .psp, .pdb, .dxf, .dwg, .drw, .casb, .ccp, .cal, .cmx, .cr2
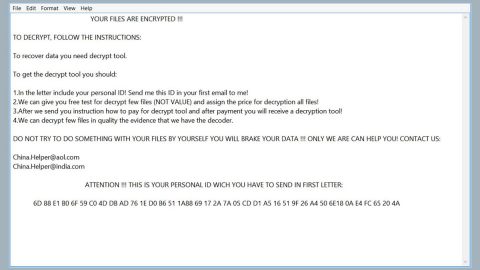
After finding its targeted files, it starts the encryption process shortly with the use of the RSA 4096 encryption algorithm. Once it finishes the encryption, it appends the .XIAOBA extension to each one of the affected files. It then releases a file named “HELP_SOS.hta” which contains the ransom note stating:
“File Recovery Gunde
You may have noticed that your file could not be opened and some software is not working properly.
This is not wrong. Your file content still exists, but it is encrypted using “XIAOBA 2.0 Ransomware”.
The contents of your files are not lost and can be restored to their normal state by decryption.
The only way to decrypt a file is to get our ”RSA 4096 decryption key” and decrypt it using the key.
Please enter 0.5 bitcoin into this address: lDveXPhdwz69ttF822keJT2uxl onaDrzyb
Please contact E-Mail after completing the transaction: [email protected]
Send the file that needs to be decrypted to complete the decryption work
Using any other software that claims to recover your files may result in file corruption or destruction.
You can decrypt a file for free to ensure that the software can recover all your files.”
How is the malicious payload of XIAOBA 2.0 ransomware distributed over the web?
The malicious payload of XIAOBA 2.0 ransomware is named “Uninstaller”, which according to security experts, may have come embedded in a legitimate program that victims have downloaded thinking that it was some sort of a program that they’ll use often. In other words, XIAOBA 2.0 ransomware might spread as a fake software or software update. Thus, you must be careful in downloading programs and updates over the web and make sure that if you do, you obtain these installers or updates from trusted sites and not third-party ones.
Make sure to follow each one of the removal steps laid out below to obliterate XIAOBA 2.0 ransomware from your computer successfully.
Step 1: Close XIAOBA 2.0’s ransom note displayed on your screen.
Step 2: Launch the Task Manager by simply tapping Ctrl + Shift + Esc keys on your keyboard.
Step 3: Under the Task Manager, go to the Processes tab and look for a process named “Uninstaller 30.0” or any other suspicious-looking process which takes up most of your CPU’s resources and is most likely related to XIAOBA 2.0 ransomware.

Step 4: After that, close the Task Manager.
Step 5: Tap Win + R, type in appwiz.cpl and click OK or tap Enter to open Control Panel’s list of installed programs.
Step 6: Under the list of installed programs, look for XIAOBA 2.0 ransomware or anything similar and then uninstall it.

Step 7: Next, close Control Panel and tap Win + E keys to launch File Explorer.
Step 8: Navigate to the following locations below and look for XIAOBA 2.0 ransomware’s malicious components such as HELP_SOS.hta and Uninstaller 30.0 as well as other suspicious files, then delete all of them.
- %TEMP%
- %WINDIR%\System32\Tasks
- %APPDATA%\Microsoft\Windows\Templates\
- %USERPROFILE%\Downloads
- %USERPROFILE%\Desktop
Step 9: Close the File Explorer.
Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use [product-name], this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then, by all means, go on to the next steps.
Step 10: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 11: Navigate to the following path:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\Background
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Personalization
- HKEY_CURRENT_USER\Control Panel\Desktop\ScreenSaveTimeOut
- HKEY_CURRENT_USER\Control Panel\Desktop
Step 12: Delete the registry keys and sub-keys created by XIAOBA 2.0 ransomware.
Step 13: Close the Registry Editor and empty the Recycle Bin.
It is important to make sure that nothing is left behind and that XIAOBA 2.0 ransomware is completely wiped out from your system. To do that, use the following antivirus program.
Perform a full system scan using [product-code]. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in the URL address, [product-url] in the Run dialog box and then tap Enter or click OK.
- After that, it will download the program. Wait for the download to finish and then open the launcher to install the program.
- Once the installation process is completed, run [product-code] to perform a full system scan.
- After the scan is completed click the “Fix, Clean & Optimize Now”button.