What is Jhash ransomware? And how does it execute its attack?
Jhash ransomware is another variant of the infamous open source platform known as Hidden Tear. This open source platform has been used too many times by cyber criminals in creating ransomware infections and has already spawned countless ransomware threats one of which is the Jhash ransomware. This new ransomware first emerged on November 08, 2017. According to researchers, it mainly targets users from Venezuela. But that does not mean that it won’t affect other users as well as it uses a common distribution method to proliferate.
During its attack, Jhash looks for files to target on the infected computer and the following are the file types it most likely includes in its attack:
.3dm, .3g2, .3gp, .7zip, .aaf, .accdb, .aep, .aepx, .aet, .ai, .aif, .as, .as3, .asf, .asp, .asx, .avi, .bmp, .c, .class, .cpp, .cs, .csv, .dat, .db, .dbf, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .dxf, .efx, .eps, .fla, .flv, .gif, .h, .idml, .iff, .indb, .indd, .indl, .indt, .inx, .jar, .java, .jpeg, .jpg, .js, .m3u, .m3u8, .m4u, .max, .mdb, .mid, .mkv, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .msg, .pdb, .pdf, .php, .plb, .pmd, .png, .pot, .potm, .potx, .ppam, .ppj, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prproj, .ps, .psd, .py, .ra, .rar, .raw, .rb, .rtf, .sdf, .sdf, .ses, .sldm, .sldx, .sql, .svg, .swf, .tif, .txt, .vcf, .vob, .wav, .wma, .wmv, .wpd, .wps, .xla, .xlam, .xll, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xqx, .zip.
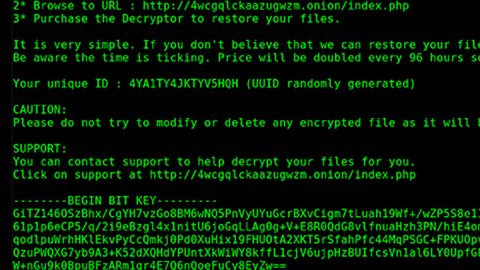
There is nothing unique about Jhash ransomware because just like a typical ransomware, it encrypts user-generated files and mark the encrypted files with the file extension, .locky – because of the extension it uses, some experts wondered if it could be related to the notorious Locky ransomware but there seems to be no proof that these two are related other than the obvious fact that Jhash uses the .locky extension in marking the affected files. On the encryption process, Jhash uses a combination of RSA and AES encryption algorithms so it would be hard to recover the encrypted files unless you have a decryption key. Jhash delivers its ransom note in file named Leeme_Nota_de_Rescate.txt. Here’s the ransom note translated into English:
“This computer has been hacked,
Your personal information has been encrypted, you send us $ 10 through PAYZA to the following payment address: [email protected], and you will send a screenshot of the transaction to the same email. After that, we will send you a guide to recover your precious files. One wrong step and you will lose all your files, do not make mistakes.”
Aside from delivering the ransom note, this ransomware also changes the desktop wallpaper containing the following message:
“You should not be scared … But we have blocked all your files so that they are unusable.
If you want to unlock them … Open the File Readme.txt that is on your desktop. And carefully follow the instructions.
One wrong step and there will be irreparable damage.”
How does Jhash ransomware proliferate?
Malicious spam email campaign is Jhash ransomware’s chosen distribution method to proliferate. Usually, cyber crooks sends thousands of spam emails containing malicious attachment. These kinds of emails are usually disguised as something important or something that would definitely catch users’ attention and pique their curiosity so that they’ll open the email and download its attachment which is why you should be wary of any suspicious-looking emails no matter who sent them and keep your antivirus program and your system updated at all times.
Refer to the given steps below to terminate Jhash ransomware from your PC.
Step 1: Tap Ctrl + Shift + Esc keys to open the Task Manager.

Step 2: After opening the Task Manager, look for Jhash ransomware’s malicious process such as local.exe, right click on it and select End Process or End Task.

Step 3: Close the Task Manager and open Control Panel by pressing the Windows key + R, then type in appwiz.cpl and then click OK or press Enter.
Step 4: Look for Jhash ransomware or any suspicious program and then Uninstall it/them.

Step 5: Tap Win + E to launch File Explorer.
Step 6: After opening File Explorer, navigate to the following locations below and look for Jhash ransomware’s malicious components such as ransom.jpg, a folder named Rand123, Leeme_Nota_de_Rescate.txt and READ_IT.txt.locky as well as the malicious executable file responsible for installing the crypto-malware in your computer.
- C:\Users\<your username>\AppData\Local\Temp
- %HOMEDRIVE%
- %USERPROFILE%\Desktop
- %USERPROFILE%\Downloads
- %AppData%
- %Local%
- %Temp%
- %Roaming%
- %LocalLow%
Step 7: Close the File Explorer. Before you proceed to the next steps below, make sure that you are tech savvy enough to the point where you know exactly how to use and navigate your computer’s Registry. Keep in mind that any changes you make will highly impact your computer. To save you the trouble and time, you can just use PC Cleaner Pro, this system tool is proven to be safe and excellent enough that hackers won’t be able to hack into it. But if you can manage Windows Registry well, then by all means go on to the next steps.
Step 8: Tap Win + R to open Run and then type in regedit in the field and tap enter to pull up Windows Registry.

Step 9: Navigate to the listed paths below and look for the registry keys and sub-keys created by Jhash ransomware.
- HKEY_CURRENT_USER\Control Panel\Desktop\
- HKEY_USERS\.DEFAULT\Control Panel\Desktop\
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
Step 10: Delete the registry keys and sub-keys created by Jhash ransomware.
Step 11: Close the Registry Editor.
Step 12: Empty your Recycle Bin.
To make sure that Jhash is completely removed and that nothing is left behind, use the following antivirus program. To use it, refer to the instructions below.
Perform a full system scan using SpyRemover Pro. To do so, follow these steps:
- Turn on your computer. If it’s already on, you have to reboot
- After that, the BIOS screen will be displayed, but if Windows pops up instead, reboot your computer and try again. Once you’re on the BIOS screen, repeat pressing F8, by doing so the Advanced Option shows up.
- To navigate the Advanced Option use the arrow keys and select Safe Mode with Networking then hit
- Windows will now load the SafeMode with Networking.
- Press and hold both R key and Windows key.
- If done correctly, the Windows Run Box will show up.
- Type in explorer http://www.fixmypcfree.com/install/spyremoverpro
A single space must be in between explorer and http. Click OK.
- A dialog box will be displayed by Internet Explorer. Click Run to begin downloading the program. Installation will start automatically once download is done.
- Click OK to launch it.
- Run SpyRemover Pro and perform a full system scan.
- After all the infections are identified, click REMOVE ALL.
- Register the program to protect your computer from future threats.